Hot Gadget Hacks How-Tos


How To: Make a shake microphone out of a flashlight
Watch as Kipkay from MAKE Magazine shows you how to make something really cool for a shake microphone, with parts from RadioShack. You'll be transforming a simple shake flashlight into a so-called shake microphone. The fun won't stop when you hear your shaky voice out loud.

How To: Make noise canceling headphones
Kipkay explains how to make noise canceling headphones. You can make them without spending much money. You need Howard Leight earmuffs and a small pair of headphones, but you start by disassembling the headphones.

How To: Make noise canceling headphones and an LED light
Let Forbes help you make a few do-it-yourself projects in record breaking time. This video tutorial contains information on how to make three various projects. Learn how to make your very own noise canceling earphones out of junk old headphones, make an LED light, and make a simple marshmallow shooter. This projects are not only easy and quick to make, but fun. Make noise canceling headphones and an LED light.

How To: Repair an HP iPAQ RX3100, 3400 or 3700 PDA
Need a quick repair job for your HP iPAQ Pocket PC RX3100, 3115, 3400, 3415, 3417, 3700, or 3715? Well, this video tutorial will show you how to disassemble the phone after it's been damaged. You'll see exactly how to take it apart, then simply reverse the instructions to put the HP iPAQ RX3100, 3115, 3400, 3415, 3417, 3700, or 3715 back together.

How To: Repair an HP iPAQ H4150 or H4155 PDA
Need a quick repair job for your HP iPAQ Pocket PC H4150 or H4155? Well, this video tutorial will show you how to disassemble the phone after it's been damaged. You'll see exactly how to take it apart, then simply reverse the instructions to put the HP iPAQ H4150 or H4155 back together.
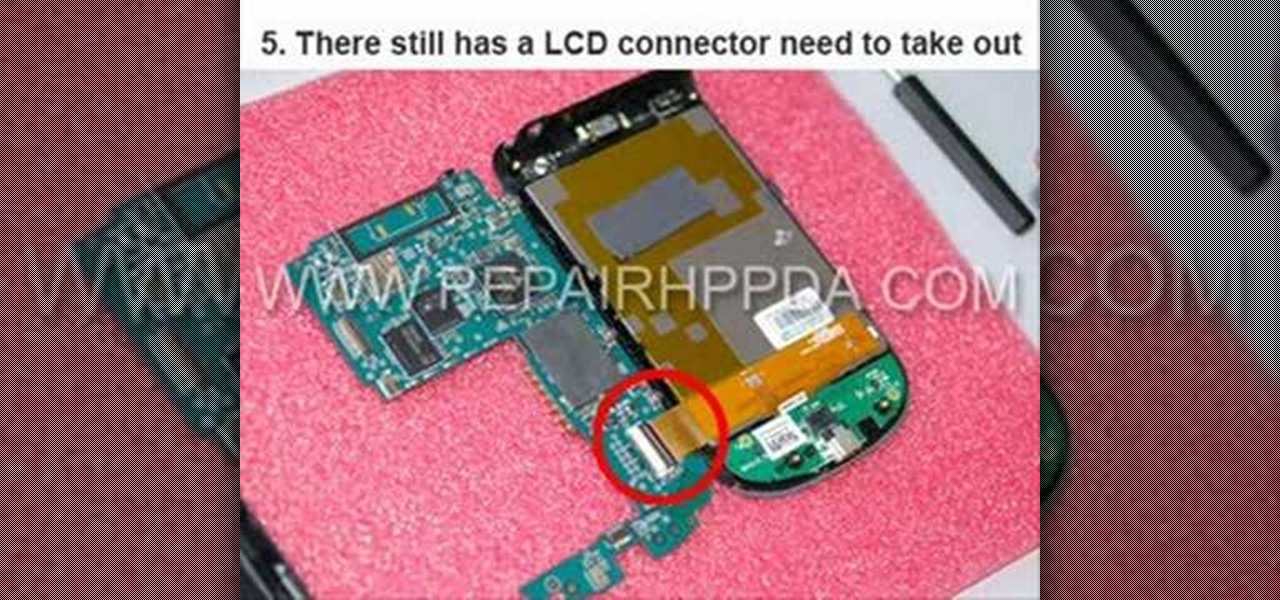
How To: Repair an HP iPAQ 110, 111, 112, 114, or 116 PDA
Need a quick repair job for your HP iPAQ Classic Handheld Pocket PC 110, 111, 112, 114, or 116? Well, this video tutorial will show you how to disassemble the phone after it's been damaged. You'll see exactly how to take it apart, then simply reverse the instructions to put the HP iPAQ 110, 111, 112, 114, or 116 back together.
How To: Find MP3s with the Google search engine
Find MP3 files using Google by typing in the name of the song using quotation marks. Locate MP3 files with tips from a professional musician in this free video on music.

How To: Replace an LCD screen in an HP iPAQ H2210 or H2215 PDA
Need a quick repair job for your HP iPAQ Pocket PC H2210 or H2215? Well, this video tutorial will show you how to replace the LCD screen after it's been damaged. You'll see exactly how to take the old one out, then simply reverse the instructions to put the new LCD screen into the HP iPAQ Pocket PC H2210 or H2215 PDA.

How To: Find lyrics to an unknown song with Google search
Find lyrics to an unknown song by logging on to the Internet and typing in a few words from that song into a search engine. Locate lyrics to an unknown song with tips from a professional musician in this free video on music.

How To: Find song lyrics online
Get that song you heard on the radio out of your head and into your record collection with this how-to, which will teach you how to find song information using the Google search engine. Find a song by accessing the Internet and typing in lyrics using quotation marks. Learn to find a song with tips from a professional musician in this free video on music.

How To: Do some basic soldering for electronic equipment
Need a little help soldering? If you can't quite figure out how to solder for your electronics and wires, maybe it's time you took a soldering 101 class. Well, no need to pay any expensive tuition, just watch this video tutorial to see how to do some basic soldering for electronic equipment or whatever you need it for. It's as simple as getting some solder and a soldering gun. The rest comes naturally, believe me. This explanation is more that enough to get your started in the world of solder.

How To: Make a cheap iPod wall charger
If you would like an iPod wall charger, but don't want to spend all of that money at Apple, just watch this video tutorial to see how to make a cheap iPod wall charger with just an old cell phone charger and a USB extension. There's no need to spend a bunch of money, just use the junk that's lying around your home. Electrical tape always comes in handy too, so remember that. Scissors, too.
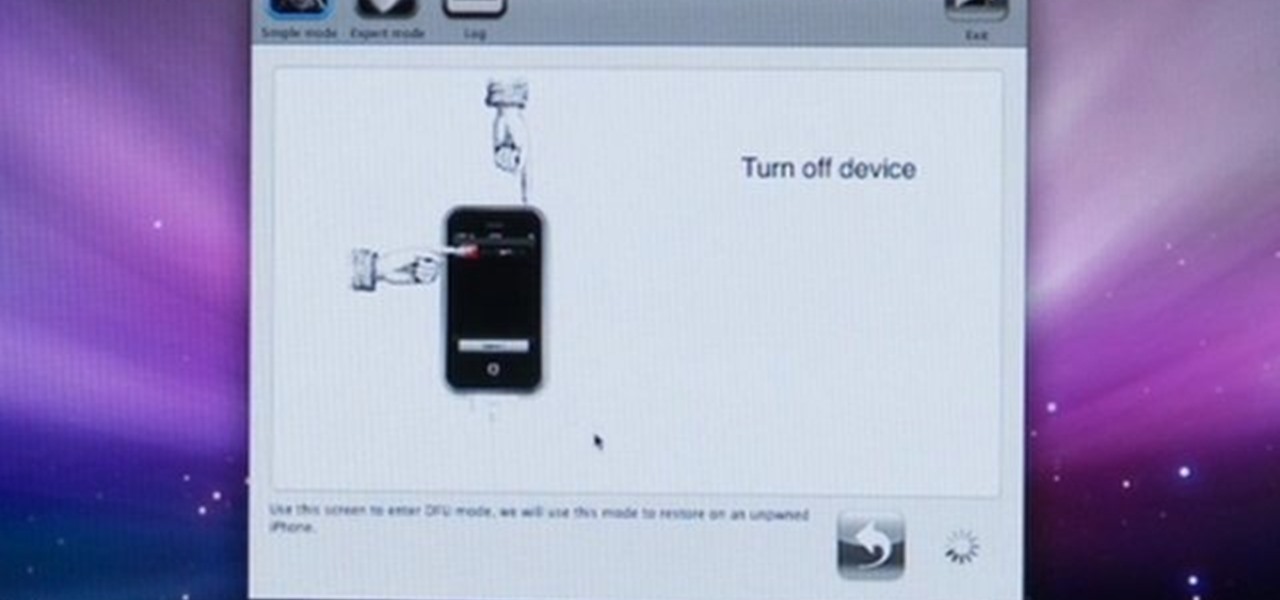
How To: Jailbreak an iPhone with PwnageTool 2.0.1
This video tutorial will show you how to use the Dev Team PwnageTool 2.0.1 to Jailbreak and unlock the orignal iPhone with 2.0 software update. This is also how to jail break the iPhone 3G on Mac and Windows. It can't get any easier than watching this easy to follow video. Jailbreaking is easy... and worth it.

How To: Illuminate a regular computer keyboard
Light up your keyboard with this illuminating tutorial from Make Magazine's Kipkay. To get started on this hack, which should take roughly a half an hour and cost no more than $5, you'll need the following: (1) a regular computer keyboard (most any model will do), (2) a screwdriver, (3) a drill, (4) telephone wire, (5) heat shrink tubing, and (6) two 5 mm high-brightness, white LEDs. For comprehensive, step-by-step instructions on building your own light-up keyboard, simply watch this hacker'...

How To: Jailbreak 2.0.2 the iPhone or iPod Touch
Check out this video tutorial to see how to jailbreak 2.0.2 the iPhone or iPod Touch. We all know about Jailbreaking, so get your Apple iPhone or iPod Touch in sync with the rest of the world... hack it. Nobody like a party pooper, so jailbreak it just like everyone else. Seriously, don't miss out on this awesome experience.

How To: Jailbreak your Apple iPhone 3G using QuickPwn
In this video tutorial, you will see how to jailbreak your Apple iPhone 3G using QuickPwn (these steps will work for the iPhone, iPhone 3G, and the original iPod Touch). By the way, this program, which is free, will work on both Windows and MAC OS X.

How To: Make music with a microcontroller
Learn how to use a piezoelectric element as a speaker, and how to generate musical notes with a microcontroller with this home electronics how-to. For more on programming microcontrollers to make sweet, sweet music, watch this helpful video guide.

How To: Strip insulated copper wire for electronics
This video tutorial explains how to strip insulated wire the right way. You'll learn how to adjust your wire strippers to make the process easier. Some people don't even use wire strippers, they use a knife or maybe even their teeth, but this causes nicks in the copper. To get the insulation off with ease and without gouges in the copper wire, use the proper sized wire strippers and adjust them right to fit the gauge of your wire. It's as simple as that. You don't need to go to vocational sch...

How To: Make LED and basic sink tube lightsabers
Have you become a Jedi in your Star Wars delusional mind? If so, break out of the the asylum with a Jedi lightsaber. Oh, but you don't have a lightsaber yet, okay. Well, this video tutorial will show you how to make a very inexpensive LED light saber with the most basic parts you could find. Novastar will shares his Jedi wisdom on LED light sabers, so pay attention, or you could never get out of that loony bin.

How To: Wire up crystal focus boards for Jedi lightsabers
Watch as Novastar and Gundamaniac demonstrate detailed wiring for a crystal focus board for Star Wars Lightsabers! Making your very own Jedi Light Saber may be a daunting task if you don't know what you're doing, but this four-part video tutorial will save the day from evil forces. To start off wiring the CF board, make sure you have your SanDisk on it already.

How To: Stream webcam live video on a WebStarts website
WebStarts.com is a free website creation and hosting interface with a powerful drag-and-drop design interface. In this video tutorial, you'll learn how to add streaming video to your WebStarts website. For more information, and to get streaming live video from your own WebStarts site, watch this web design video tutorial.

How To: Sign up for Blogger account
logger is a free blog publishing tool from Google for easily sharing your thoughts with the world. Blogger makes it simple to post text, photos and video onto your personal or team blog. This video tutorial will walk you through the Blogger signup process. For more information, and to get started creating your own blog, watch this video guide.

How To: Secure your website with AccessDiver
AccessDiver is a website security scanner. It incorporates a set of powerful features that will help you to find and organize vulnerabilities and weaknesses in your own site. This video tutorial presents a guide to its use. For more information, as well as to get started using AccessDiver for yourself, watch this video tutorial.

How To: Use the LastPass Password Manager
LastPass is a free password manager and form filler that makes your web browsing easier and more secure. This video tutorial presents a basic introduction, demonstrating the basics of using the LastPass Password Manager. Learn how to use LastPass with this how-to.

How To: LastPass Form Fill Demonstration
LastPass is a free password manager and form filler that makes your web browsing easier and more secure. This video tutorial presents a simple demonstration of new Form Fill feature from LastPass. Take a look.

How To: Download pictures from Orkut
Downloading pictures from Orkut, Google's social networking site, is simple and can be accomplished in five steps. First, log into Orkut. Second, open the image you want to save. Third, drag the image to your web browsers address bar. Fourth, right click and select Save Picture As. Voilà. There's nothing to it. Save pictures from Orkut with this video tutorial.

How To: Hack with Hacme Shipping
Foundstone Hacme Shipping is a web-based shipping application developed by Foundstone to demonstrate common web application hacking techniques such as SQL Injection, Cross Site Scripting and Escalation of Privileges as well as Authentication and Authorization flaws and how they are manifested in the code. Written in ColdFusion MX 7 using the Model-Glue framework and a MySQL database, the application emulates the on-line services provided by major shipping companies. This video will get you st...

How To: Make a website a search engine sponge
With the advent of Web 2.0 sites and tools, building your own small business marketing website has never been easier. This video SEO tutorial demonstrates a WordPress plugin called SEO Friendly Images. Once installed, all the images on your blog are automatically optimized to be gulped up by search engines. For more, and to get started using SEO Friendly Images for yourself, watch this helpful video guide.

How To: Organize a Web site for Google search
This video tutorial explains how to structure your web site the right way using content silos. But what's a content solo, you ask? Watch this video SEO tutorial to find out. Make structural improvements to your website such that Google has an easier time isolating your keywords with this how-to.
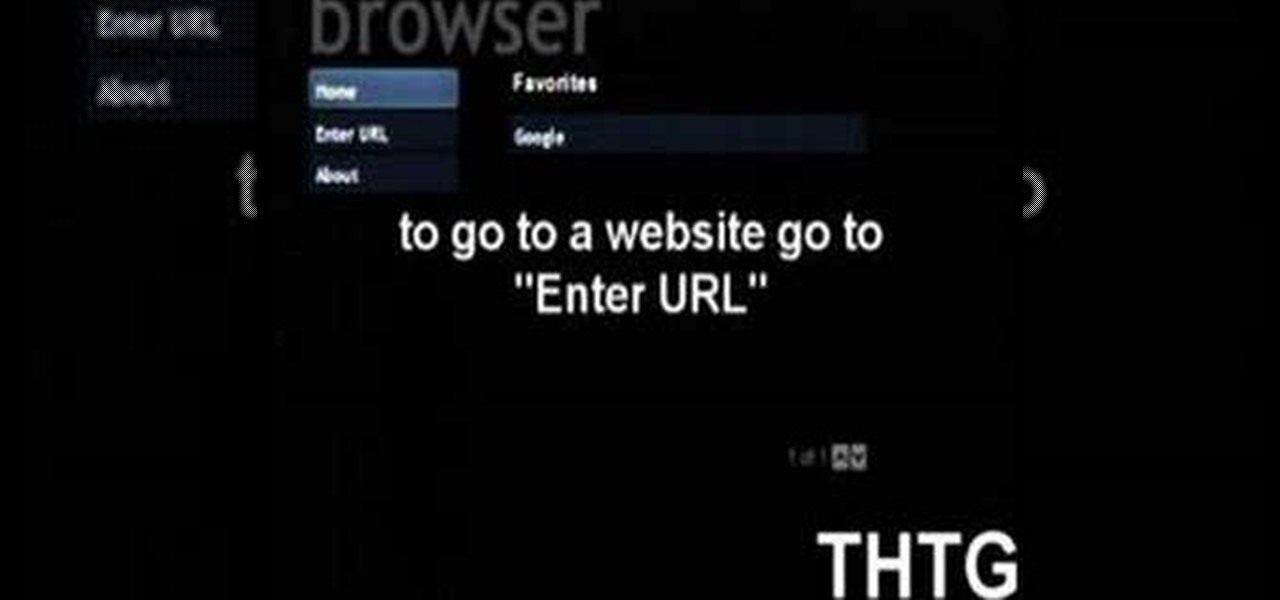
How To: Get an Internet Browser on an Xbox 360 Game Console
This handy video tutorial presents instructions for getting an Internet browser on your Xbox 360 game console without any mods. All you'll need to follow along is to configure Xbox Media Center, or XMBC, to use the computer you use to surf the Internet. Get a web browser on your Xbox with this how-to!
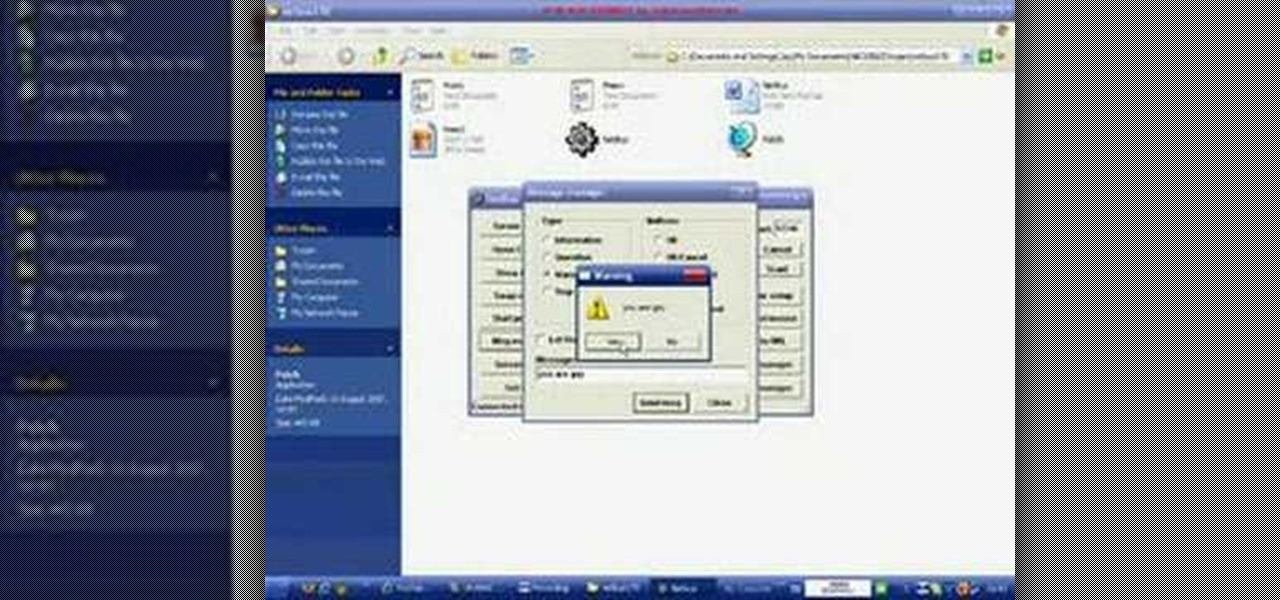
How To: Hack with NetBus 1.7
NetBus—Swedish for NetPrank—is a Trojan horse application that will allow you to remotely control any Windows system that runs it (provided that system is not running anti-virus software). For more information, and to get started using the NetBus hacking tool for yourself, watch this video guide.

How To: Fancify your MySpace profile with div overlays
CSS div layers permit you to abandon the traditional MySpace layout by covering it up with a blank slate. Then you can create virtually anything you want to. You can add images, tables, Flash documents—most anything you can think of. For more information, and to get started using CSS div layers on your own MySpace profile, watch this helpful video guide.
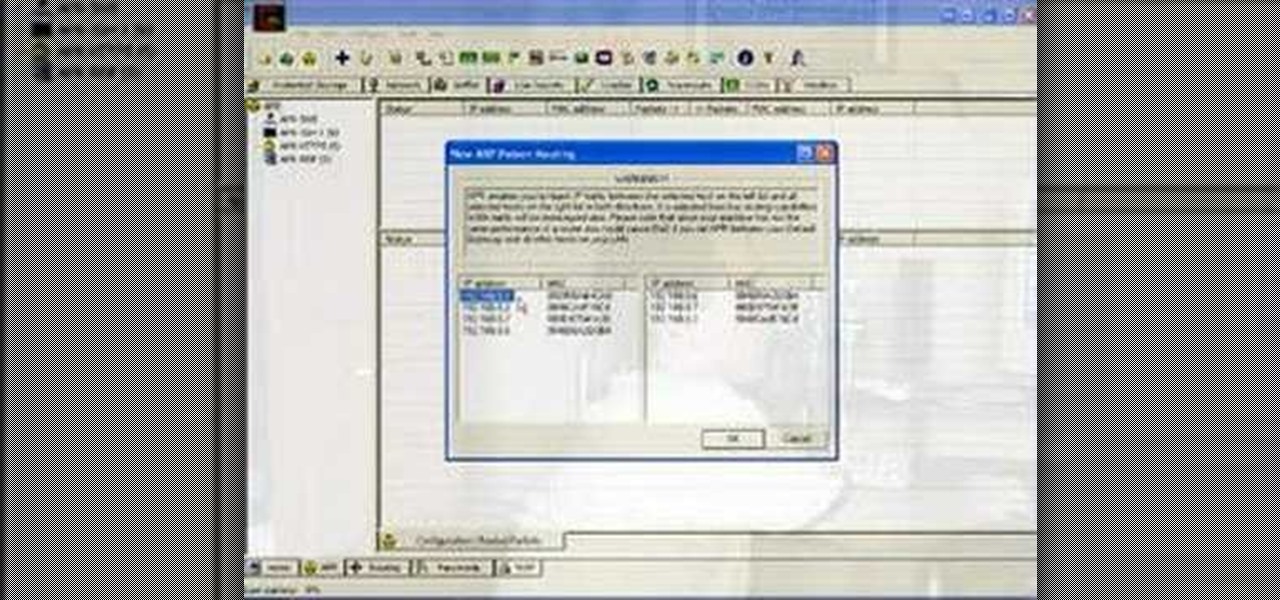
How To: Hack VOIP sessions with Cain
Jared of the TechCentric crew gives you the lowdown on the basics of keeping your VoIP conversations secure and, on the other side of things, how to use the Cain VoIP sniffing application. For detailed instructions on keeping your VoIP conversations private, watch this hacking how-to.

How To: Protect your site from hacker attacks with Google
They are after you from all over the globe. Looking for ways to exploit you. Ways to hurt you. Not political terrorists, but rather "info terrorists." Each month thousands of websites get hacked into and have hidden links inserted into the pages by people wanting their spam sites to rank highly in the search engines.

How To: Keep email private with MixMaster
Email is one of the least private and least secure forms of communication, although few people realize this. MixMaster is one way to allow secure, anonymous communication even over the very public medium of email. This tutorial will get you started with MixMaster quickly and easily.

How To: Hack a NETBIOS IPC$ share
In this video tutorial, a CEH-certified Ethical Hacker will teach you how to exploit the old netbios remote IPC$ share while also demonstrating the beginning stages of a successful network security audit. For more

How To: Use the ActiveX Opt-In feature in Internet Explorer 7
Web browsers such as Windows Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Microsoft Internet Explorer 7 has several new features that make using the web easier and safer than ev...

How To: Use the protected browsing mode in Internet Explorer 7
Web browsers such as Windows Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Microsoft Internet Explorer 7 has several new features that make using the web easier and safer than ev...

How To: Use the Internet Explorer 7 phishing filter
Check out this video tutorial to learn more about the Phishing Filter on Internet Explorer 7. Web browsers such as Microsoft's Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Inter...
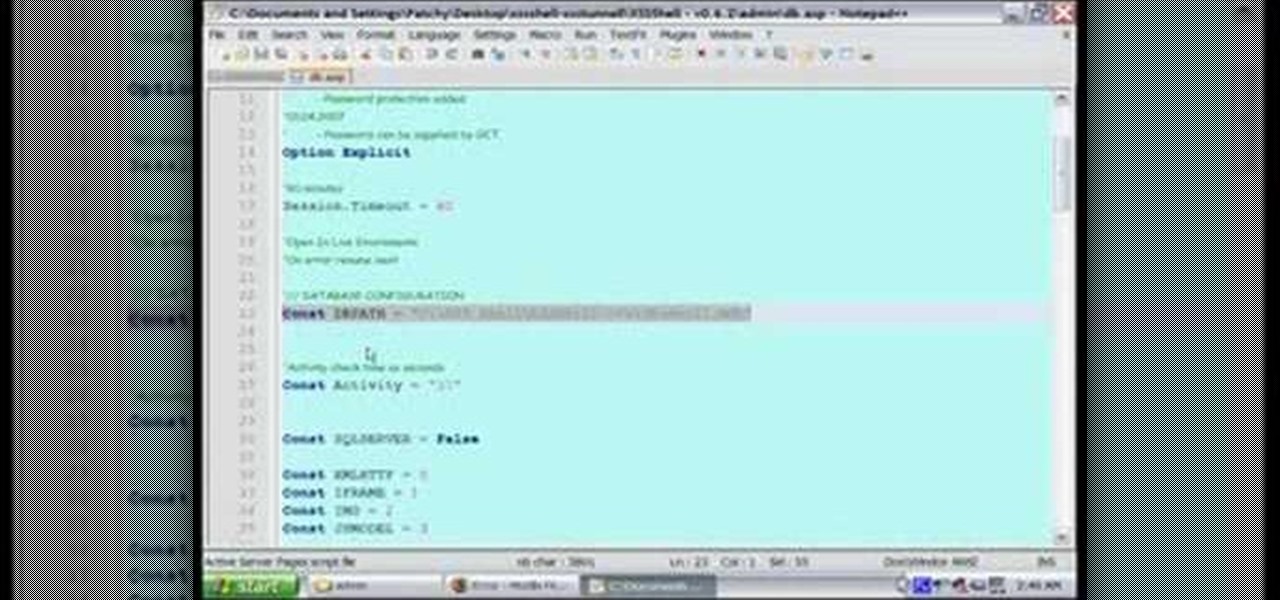
How To: Hack a remote Internet browser with XSS Shell
XSS Shell is a cross-site scripting backdoor into the victim's browser which enables an attacker to issue commands and receive responses. During a normal XSS attack an attacker only has one chance to control a victim's browser; however, the XSS Shell keeps the connection between the attacker and the victim open to allow the attacker to continuously manipulate the victim's browser. XSS Shell works by setting up an XSS Channel, an AJAX application embedded into the victim's browser, that can ob...