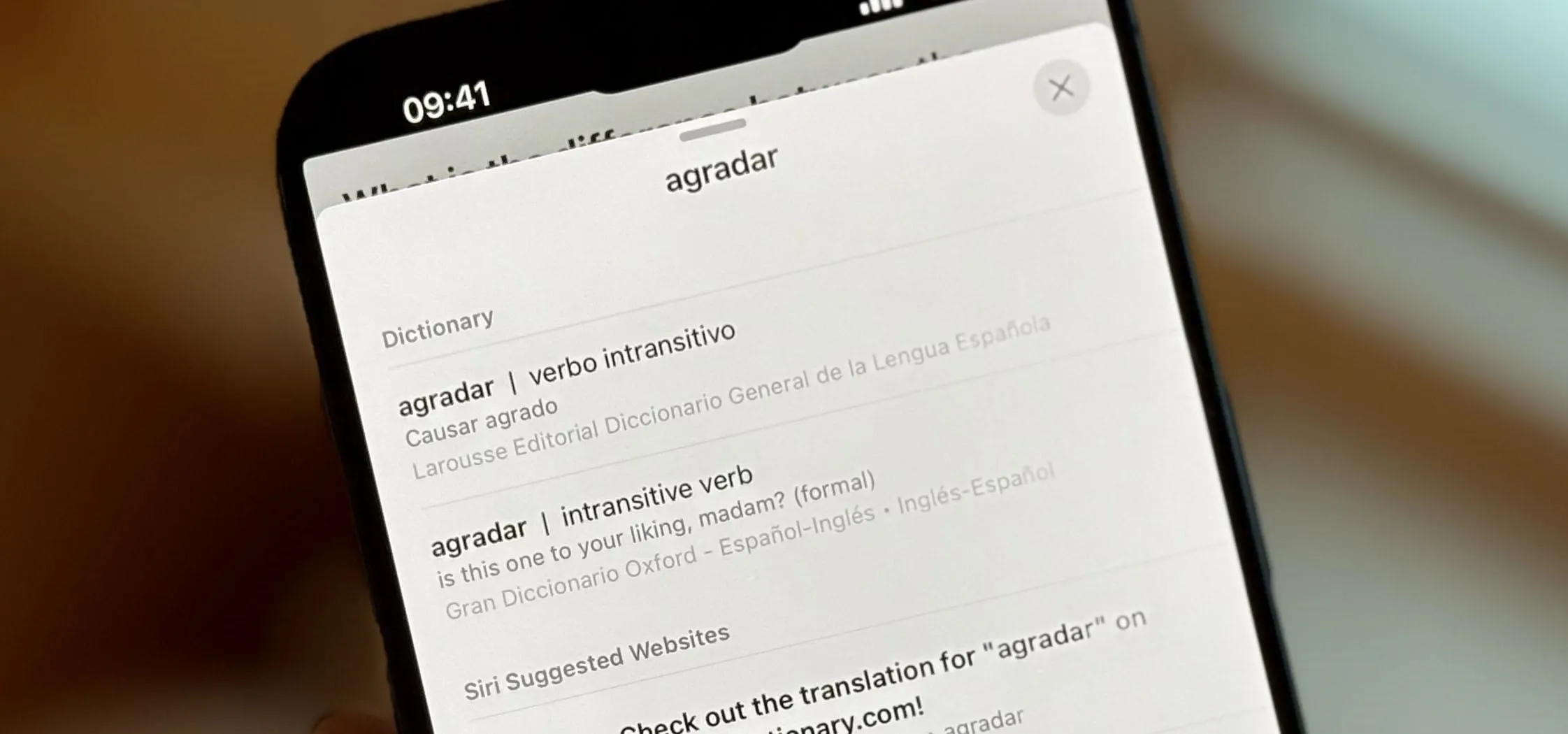
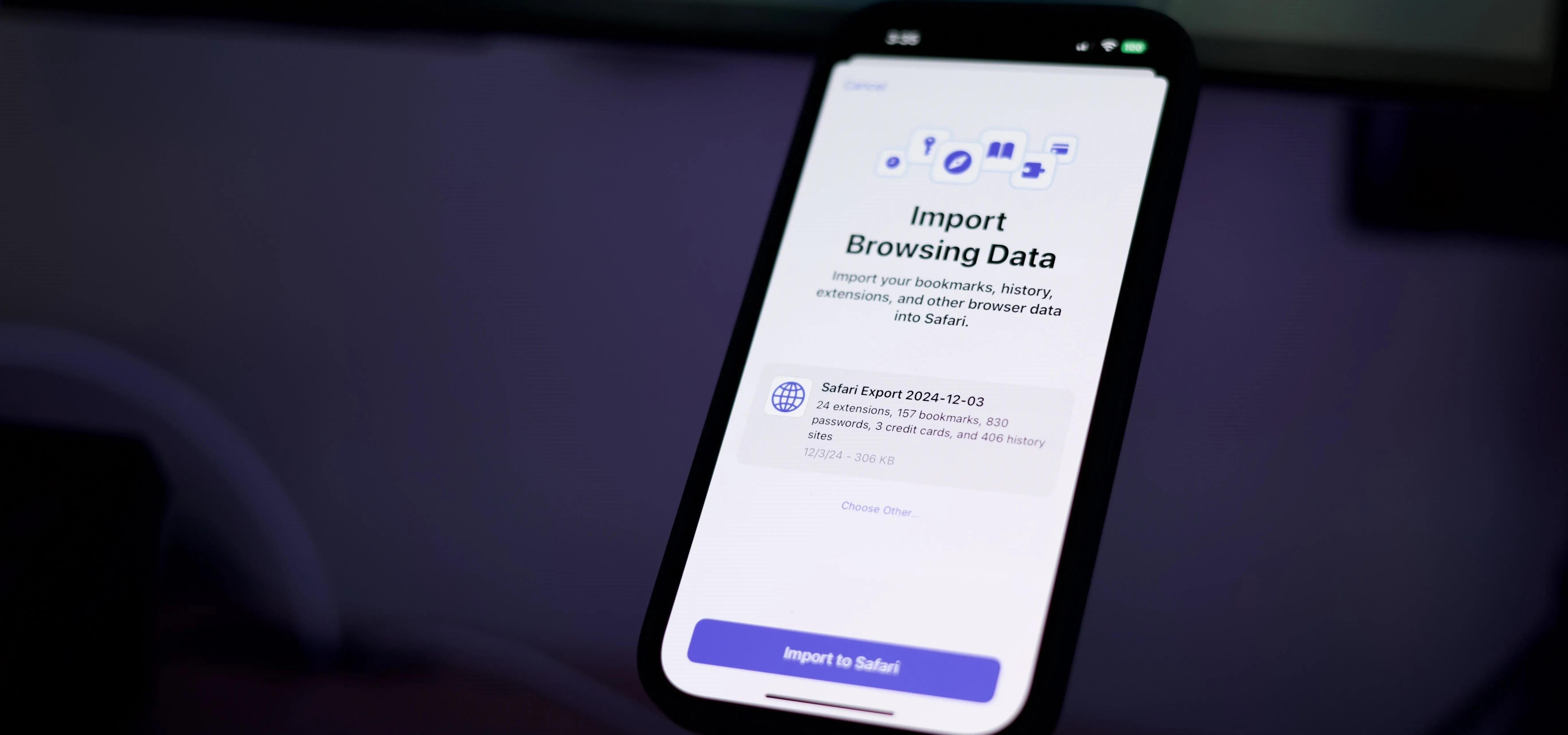
Gadget Hacks: How To's
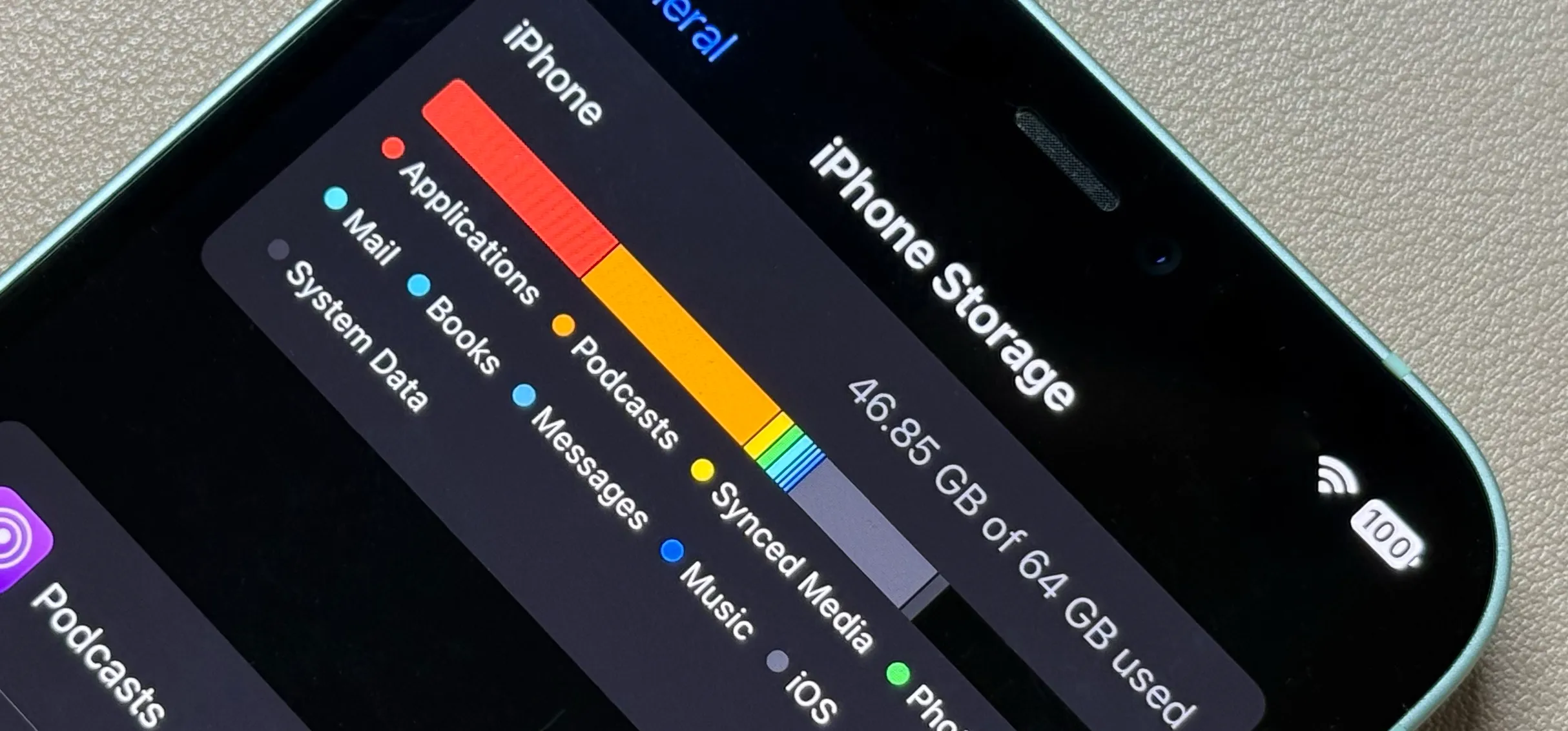
how to
The Ultimate Guide to Freeing Up Storage Space on Your iPhone
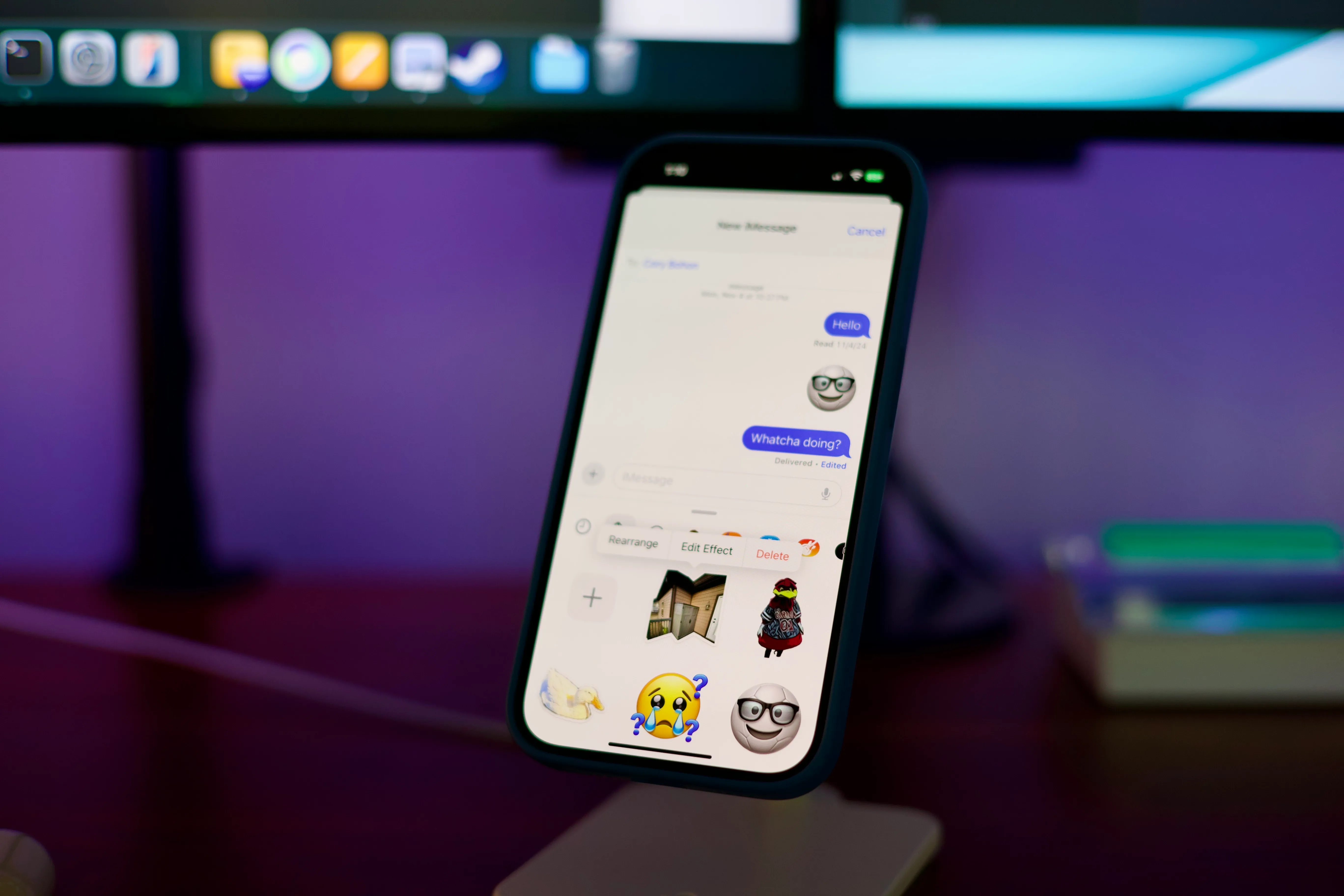
how to
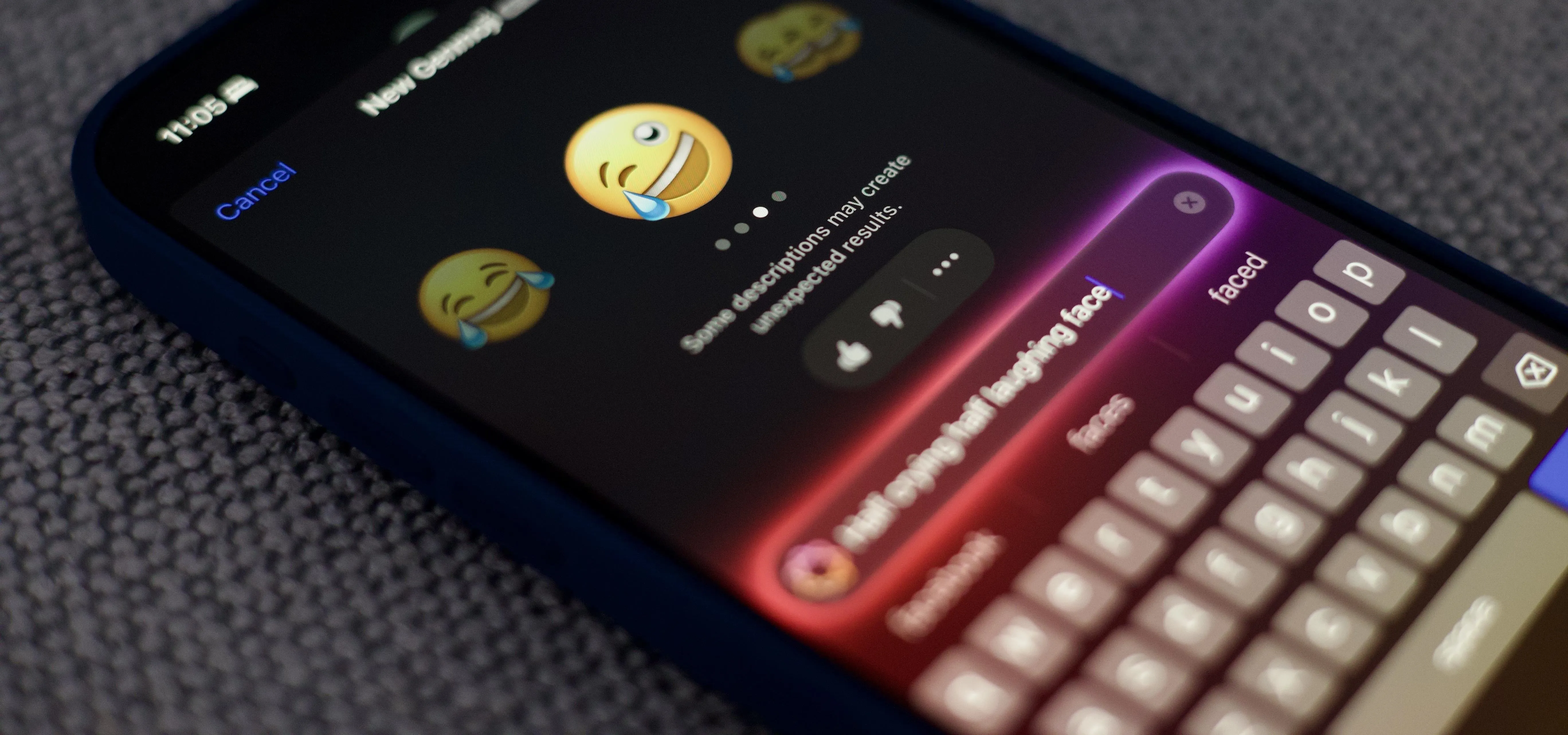
How to Delete Custom Stickers on Your iPhone, iPad, or Mac — From Messages or the Keyboard

how to
Feel Who's Calling or Texting with Custom Vibration Alerts on Your iPhone